Not all fingerprint sensors are created equal — here’s what to look for
Fingerprint sensors are increasingly being used to secure laptops, five years after the iPhone 5S made them common on smartphones.
But in a rush to equip even inexpensive laptops with fingerprint sensors — often using the same parts that are used on phones — laptop makers may be overlooking one key security feature.
Some fingerprint sensors don’t protect or encrypt the information passed between the sensor itself and the computer they are embedded in, says Godfrey Cheng, who’s a VP of marketing at Synaptics, which makes fingerprint sensors.
So if an attacker can get between the fingerprint sensor and the computer, then the attacker can steal an image of the user’s fingerprint and make a physical copy. Synaptics demonstrated this to me in a staged demo that resulted in a “spoof” of my fingerprint printed on a consumer printer that could unlock my iPhone, which has never been compromised — I hope.
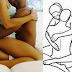
The spoof was a tiny piece of photo paper printed with conductive ink. Using this tiny strip of paper, anyone could unlock my iPhone through its fingerprint sensor. Here’s what the “spoof” looked like, although I have blurred my fingerprint for obvious reasons:
Business Insider
Here’s the demo setup:
Synaptics
It’s important to note that this demo required Synaptics to physically access these laptops, and install a device inside — and then have physical access to my iPhone. When your laptop has been compromised physically, all bets are off. At that point, you’ve already been “owned” as hackers like to say, and the only question becomes what levels of access the compromising party will obtain, and whether or not that could extend to other devices, like your iPhone.
But the demo underscores Snynaptics’ point that if computer makers use outdated or insecure parts when building a laptop, it’s feasible for a future compromise on the device to lead to other devices like your phone being compromised, a potential concern for big enterprises or government agencies that issue those models to their workers.
“You open up everybody whether it’s Apple or Windows if you are wiretapped,” Cheng said, referring to putting a device between the fingerprint sensor and the main laptop processor. “Unencrypted buses are a danger.”
The good news for Apple users is it doesn’t appear as if MacBooks are vulnerable to this attack. However, Apple’s security white paper doesn’t include enough detail to really know what’s going on internally, Cheng said.
Synaptics wouldn’t list which companies are making and using these insecure sensors, but what users can do when they’re shopping for a new laptop is check in the Windows device manager to see which specific fingerprint sensor is used in that model, and do their research if this potential vulnerability is a worry. Of course, if you’re not worried about a potential scenario where your laptop is physically compromised by a malicious party — if your laptop doesn’t leave your house, for example — this shouldn’t be something to lose any sleep over.
But for big enterprises and government agencies look to decrease any chance of a compromised laptop leading to further devices like mobile phones being compromised, “Ask for a fully encrypted sensor that encrypts from fingerprint sensor to host,” Cheng said. “Partial encryption is no encryption.”
Read more stories on Business Insider, Malaysian edition of the world’s fastest-growing business and technology news website.
✍ Sumber Pautan : ☕ Business InsiderBusiness Insider
Kredit kepada pemilik laman asal dan sekira berminat untuk meneruskan bacaan sila klik link atau copy paste ke web server : http://ift.tt/2qHRQkI
(✿◠‿◠)✌ Mukah Pages : Pautan Viral Media Sensasi Tanpa Henti. Memuat-naik beraneka jenis artikel menarik setiap detik tanpa henti dari pelbagai sumber. Selamat membaca dan jangan lupa untuk 👍 Like & 💕 Share di media sosial anda!

















Post a Comment